ProfessionalCommunity Edition
Analyzing attack results
-
Last updated: June 18, 2024
-
Read time: 2 Minutes
Burp Intruder has a range of functions to help you to systematically examine a large number of results, and understand where different kinds of interesting requests appear.
Sorting results
You can sort the results quickly identify anomalous items, for example an item with HTTP status code or response length that differs from the remaining results.
To sort the table's contents, click on any column header. You can cycle through ascending, descending, and unsorted.
Copying results
To copy the contents of a column, control-click the header. This enables you to extract an aspect of the results for further analysis.
Filtering results
The display filter enables you to hide results from view. This makes it easier to work on the content you are interested in. The current display filter is described in the filter bar above the results table. Click this to open the Intruder attack results filter window.
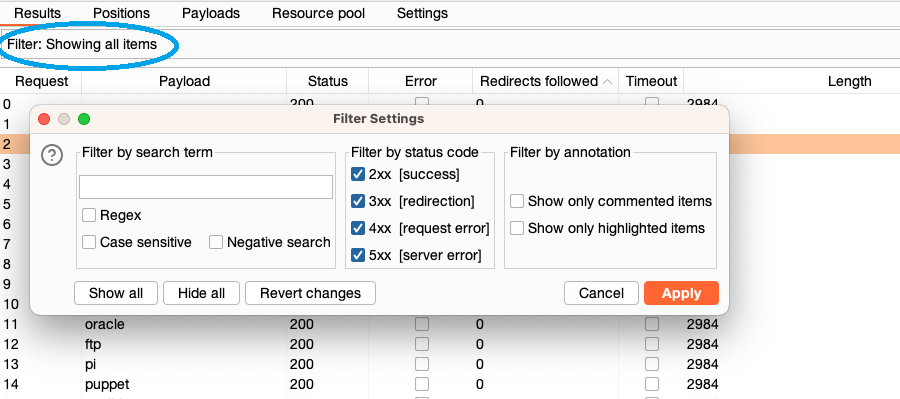
In the Intruder attack results filter window you can:
-
Filter by search term - Show or hide responses containing a specified term. You have the following options:
- Regex - Specify whether the search term is a literal string or a regular expression.
- Case sensitive - Specify whether the search term is case-sensitive.
- Negative search - Show or hide items that do not match the search term.
- Filter by status code - Show or hide responses based on their HTTP status code.
- Filter by annotation - Only show items with comments or highlights.
The filters only control what is displayed. If you hide items, they are not deleted: they reappear if you reset the filter.
Adding annotations
You can add comments and highlights to results. This enables you to flag interesting results for further investigation.
To highlight a result:
- In the results table, select one or more items from the list.
- Right-click the item and select Highlight.
- Select a color from the list.
To add a comment:
- In the results table, select one or more items from the list.
- Double-click the Comment column.
- Enter your comment in the cell.
Related pages
You can perform further actions on any results item to drive your testing workflow. For more information, see Intruder testing workflow.