When Burp Scanner finds an issue, it generates a fully customised advisory containing all relevant detail about the vulnerability, and how to reproduce it. This is in a format, and level of detail, that you can copy directly into a penetration testing report if you desire.
Let's see an example. Below, Burp has found a reflected XSS vulnerability:
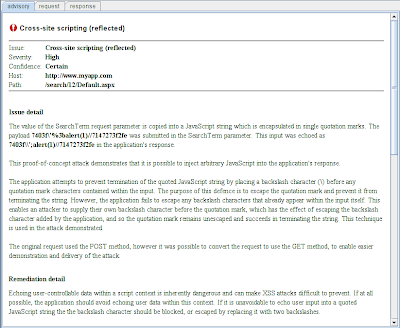
The advisory tells us:
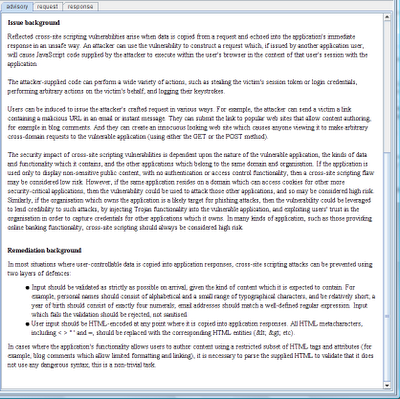
The advisory also provides some custom remediation advice, based on the observed features of the vulnerability. And in addition to the customised content, the advisory includes a "standard" description of the issue, and general defences for preventing it, enabling a less knowledgable report reader to understand the nature of the vulnerability:
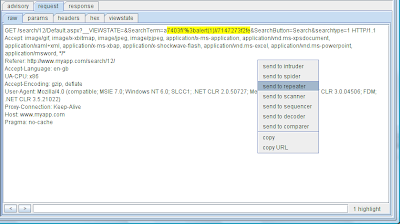
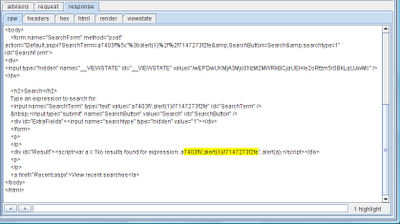
Alongside the advisory, Burp shows the requests and responses that were used to identify the issue, with relevant portions highlighted. These can be sent directly to other tools to manually verify the issue, or fine-tune the proof-of-concept attack that was generated by Burp:
When you have finished testing, you can export a report of vulnerability advisories in HTML format. To do this, you select the desired issues from the aggregated results display (you can multi-select individual hosts, folders, issues, etc.) and select "report issues" from the context menu. The reporting wizard lets you choose screen- or printer-friendly output, the level of issue description and remediation to include, whether to show request and response details in full, or extracts, or not at all, and whether to organise issues by type, severity or URL. Here is the report extract for the issue illustrated above, with all detail turned on, and showing extracts of application responses in printer-friendly format:
